We are going to discuss the strengths, weaknesses and possible security issues of passwords. Further, we will describe implicit weaknesses of some of the implementations, including the impact and risk of brute force, password guessing, awareness about presence of key loggers in public computers and prevention, phishing, a technique to hack online passwords and us will also see the most efficient technique of password cracking i.e. Rainbow table. The secondary goal is to bring awareness in mass about the possible threats they can suffer from and provide solutions by keeping a strong password. The fact is that it doesn’t do much good to lock all the doors if you leave a window open. Also, we will put some light on measures to be taken if the password is hacked. Finally, we hereby, provide a source of information containing advice and references for securing systems containing the implementations as covered in this paper.
I. Introduction to Password Paradigm
A password in the virtual world is something like a lock in the world of reality. We all maintain passwords while using networks, email accounts, devices etc. Naturally, there are people out there who want to get your passwords. Here we provide you some requisite information about how they do it and how you can protect yourself. In today’s business environment, your corporate email security strategy is only as strong as its weakest link. Those who do not use strong passwords and password practices are often their own worst enemy. The risks are real, they affect you either directly or indirectly and they can be diminished by using strong passwords and password practices. Therefore, it is no longer simply a matter of using strong passwords and changing them often. Rather, we need to adopt a more realistic approach to password use and protection.
II. FORMAL DEFINITION OF PASSWORD
A password is an information associated with an entity that confirms the entity’s identity. A password is a secret known only to you. A password provides access to a service for a specific user and is used to verify the identity of the user. The system can be your home computer, your email account, your online bank account or any web account. If your password is captured, guessed or stolen, someone could impersonate you online, steal money from your online bank account, send emails in your name or change files on your computer to name just a few of the possible outcomes.
III. NEED FOR PASSWORD PROTECTION
You may not be a billionaire to have your bank accounts over flowing but it is of prime importance to have privacy, safety, and security in your personal and professional world. While it may seem a pain to some to change their passwords very often and remember them, but once your password is cracked, whoever has found it or taken it now has access to all your information quickly and easily. A few moments of effort on your part can save you from a lot of problems later. Imagine yourself in the world without passwords. Your personal emails would have been accessed by anybody. Money in accounts would not be safe. Password protection is not perfect but it just may deter someone from stealing your data. Passwords have become the dominant means of access control to online services. With this success has come an enormous variety of attacks: each login page represents an opportunity for an attacker who is just a short sequence of characters away from someone else’s email, banking, medical or social networking accounts. Also, passwords can provide different access permissions to users. In general, anybody can access any data or information if the password is not allotted but requiring a username and password to access various sensitive areas allows you to restrict access to only a chosen few people who know the secret codes.
IV. ATTACK SCENARIOS
A number of password cracking exists. The following subsections discuss the general ways of password cracking methods and their applicability. We will describe implicit weaknesses of some of these implementations, including the impact and risk of brute force and phishing attacks and the possible use of key loggers. When performing these attacks, there are some prerequisites to obtain the passwords. One has to know how the passwords were encrypted, which encryption method is used, and what the implementation- specific properties are. The structure of a hash has to be clear.
A. Password Guessing:
The method is guessing of passwords randomly until one password works. Password guessing is made easier by revealing the personal information and having related passwords. It will take a long time and requires huge amounts of network bandwidth considerably. It is easily detected and stopped. Presume using a dictionary would save time. Such passwords are usually weak. Surveys depict that most of the users keep their family members details, personal information, their likings, famous sports teams etc
Due to lack of awareness, users’ authentication points are generally open. One can make a way to others computer through some application programs and by sending files which open their ports. Thus, gain access to victim’s data and information. Password guessing is not very sound and sophisticated technique to crack passwords because there is no surety that password will be cracked. More techniques such as brute force mechanism, phishing etc are available in the market.
B. Key loggers:
A Key logger is a way of tracking the keys struck on a keyboard by a user and letting you know, while the user is unaware that such a thing is happening. It keeps a record of every key that is struck. With advancement in technology, latest versions have the capabilities of taking screenshots and mail delivery etc. An internet cafe machine can easily be running a key logger. The roaming user has no reliable way of determining whether it is safe, and has no alternative to typing the password. Key logging is one of the most insidious threats to a user’s personal information. Passwords, credit card numbers, etc. are potentially exposed; and the incidence of key loggers in-the-wild is apparently growing rapidly.Unlike other general threats, this is not an attack that alert and sophisticated users can avoid. There are numerous freeware offerings and many of them make efforts to conceal their presence. For example, they will not show up in the Task Manager process list or installed software list. The contents can only be accessed by the owner because it leaves no trace or path to prove its existence, Key loggers usually have short-cut keys defined by the owner through which it can be opened. As things stand a user has no reliable way to determine if a machine is running a key logger or not. In this environment is there anything a user can do to protect themselves from the possible catastrophic loss of data? In Windows, user32.dll provides event handlers that any application can invoke to trap every keyboard and mouse event. The trick lies in the fact that key loggers employ very
In Windows, user32.dll provides event handlers that any application can invoke to trap every keyboard and mouse event. The trick lies in the fact that key loggers employ very low-level OS calls.The key logger sees everything but it doesn’t understand what it sees. You don’t know if the key logger is already installed. Being wise enough, one should use virtual keyboards of standard anti-viruses. Important to make you understand that key loggers identify the key pressed from the virtual keyboards of operating systems. The best way to overcome is to implement the use of standard anti-viruses. There exists a pointer between every pair of key and after you press a key, that sequence is shuffled by the anti-virus virtual keyboard but not by the operating system virtual keyboard which is easily detected by the key loggers. Also, most of the key loggers are deficient to trap mouse clicks. Hence, one should use the mouse in excess for performing a task rather than pressing a key from the keyboard if he/she suspects the existence of a key logger in the system.
C. Brute Force Approach
A brute force attack is an attack on a password, where all possible character combinations are tried. A major advantage of this method is that all passwords will be found. However, this way of attacking a password is very inefficient. It is a good and fast method for cracking short passwords, but when password lengths are longer, this method gets very slow. Due to this characteristic, this attack is most of the time performed with progressive complexity. The technique is easy to implement and reasonably fast since not much pre-computation is involved in determining the passwords to test. Also, since the search is usually linear, it is easy to interrupt the cracking process and pick it up at a later point. First, in many cases, there is the sheer size of the password space to take into account. The following simple sum describes the number pi of different possible passwords (size of the password space) for a character space of n different characters of maximum length i. For a character set which contains only the 26 alphabetic characters from a to z and which has a maximum length of 2 characters, there will be 261 +262 = 702 different passwords to consider. For some. hashes, which are still widely used in Microsoft Windows networks (a character set of 69 characters and a maximum length of 7 characters) there are 7555858447479 (roughly 7.5 * 1012 ) different possible passwords. The actual amount of time spent is not only determined by the password space, but also by the algorithm used. The actual algorithm implementation ccan dramaticallychange the time required in a real-world cracking scenario by several orders of magnitude. In the case of John the Ripper, for example, one benchmark for cracking hashes showed more than 4.9 million attempted passwords per second, whereas on the same machine a password encrypted using the MD5-based scheme used in many modern Unix implement actions could be evaluated at little more than 4000 attempts per second.
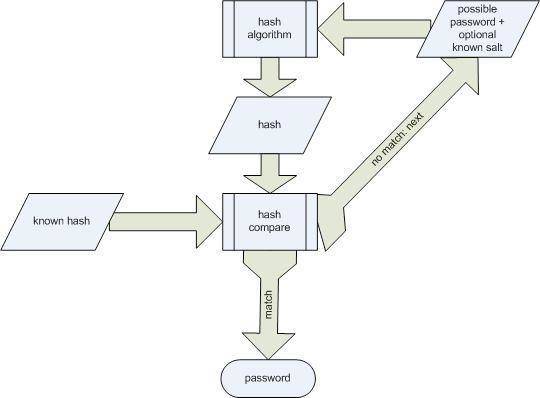
In the figure, brute force approach is shown. A hash is taken from a hashing algorithm and compared with the actual hash of the password which is already known. If it matches, the password is cracked else possible probability of the password with optional salt is matched with hashing algorithm resulting into a hash. This method is repeated until we find the correct password. Probably the most considerable disadvantage of the brute force approach is that it does not take password policies or user preferences into account. If an attacker first attempts all combinations of lowercase letters even though there are technical controls in place that demand at least one of the characters to be an uppercase letter, a lot of the attackers time will go to waste. The same consideration applies in the case of character sets that may or may not be applicable in a particular language environment. It is not wise enough to go with the approach all the time. If the passwords are short, the method is suitable to implement else better mechanisms should be used. D. Rainbow Tables Smart Rainbow table is a pre-computed lookup table, which can be used to recover the password from its hashed representation. In this, each reduction function were colored differently, the sequence of reduction functions would indeed look like a rainbow. The use of a rainbow table is much faster than a simple brute-force attack.
Key facts about Smart Rainbow Table Recovery:
1) The recovery time required depends on the number of passwords you want to recover (near to linear dependence). The more passwords you have, the longer is the recovery process.
2) The recovery time depends on a number of factors.
3) The success rate is over 99%, however, there is a small probability that Smart Rainbow Table Recovery fails.
4) recovery tables take a lot of disk space (gigabytes)
This is how the rainbow tables are implemented to crack passwords in an efficient manner. In order to recover the hashed password (which means reversing the hash), the password hash is run through the sequence of reduction functions. The structure of the rainbow table and the reduction functions guarantee that the resulting hash will match the final hash of one of the chains. Since the rainbow tables maps the final hashes of each chain to the initial plaintext password, the initial password is now known. Then the initial password is fed into the sequence of reduction functions until the original hash is found. The plaintext password used at the final iteration (which produced the original hash) is exactly the password, which is being recovered. This attack only works on algorithms that do not use salting. Though the initial cost is very high but, after the formation of the rainbow table, password matching is faster, more efficient. Also, the number of comparisons made by the approach is less than brute force approach.
E. Phishing
Phishing, also referred to as brand spoofing or carding, is a variation on “fishing,” the idea being that bait is thrown out with the hopes that while most will ignore the bait, some will be tempted into biting. The act of sending an e- mail to a user claiming to be an established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. The e-mail directs the user to visit a website where they are asked to update personal information, such as passwords and credit card, social security, and bank account numbers, that the legitimate organization already has. Using techniques and tools used by Spammers, Phishers can deliver specially crafted emails to millions of legitimate live email addresses within a few hours (or minutes using distributed Trojan networks).
One of the examples of a phishing attack: A fake MySpace login page is created by the phishers. The data is sent to various web servers which is received later. During this, 100,000 users fell for the attack before it was shut down.
Phishing e-mail messages take a number of forms:
- They might appear to come from your bank or financial institution, a company you regularly do business with, such as Microsoft, or from your social networking site.
- They might appear to be from someone you know. Spear phishing is a targeted form of phishing in which an e-mail message might look like it comes from your employer, or from a colleague who might send an e-mail message to everyone in the company, such as the head of human resources or IT.
- They might ask you to make a phone call. Phone phishing scams direct you to call a customer support phone number. A person or an audio response unit waits to take your account number, personal identification number, password, or other valuable personal data. The phone phisher might claim that your account will be closed or other problems could occur if you don’t respond.
- They might include official-looking logos and other identifying information taken directly from legitimate Web sites, and they might include convincing details about your personal information that scammers found on your social networking pages.
- They might include links to spoofed Web sites where you are asked to enter personal information. To make these phishing e-mail messages look even more legitimate, the scam artists may place a link in them that appears to go to the legitimate website but actually takes you to a phony scam site or possibly a pop-up window that looks exactly like the official site. Here are a few phrases to look for if you think an e-mail message is a phishing scam. “Verify your account.” “You have won the lottery.” “If you don’t respond within 48 hours, your account will be closed.” Ideally, desktop systems should be configured to use multiple desktop protection agents and be capable of performing services like Local Anti-Virus protection, personal firewall, anti-spam, spyware detection etc.
Emails should be HTML based in nature and should have the suitable technique to block attachment. To help prevent many Phishing attack vectors, web browser users should:
- Disable all window pop-up functionality
- Disable Java runtime support
- Disable all multimedia and auto-play/auto-execute extensions
- Prevent the storage of non-secure cookies
- Ensure that any downloads cannot be automatically run from the browser.
Also, there are a growing number of specialist anti-phishing software producers that provide browser plug-ins that prevent from unreliable links. At the client-side, protection against Phishing can be afforded by:
- Improving customer awareness
- Providing validation information for official communications
- Ensuring that the Internet web application is securely developed and doesn’t include easily exploitable attack vectors
- Using strong token-based authentication systems
- Keeping naming systems simple and understandable
Key steps to anti-phishing enterprise-level security include:
- Automatic validation of sending email server addresses,
- Digital signing of email services,
- Monitoring of corporate domains and notification of similar registrations,
- Perimeter or gateway protection agents,
- Third-party managed services.
V. Weak Passwords
A weak password is a password that is easy to detect both by humans and by computer. Usually, passwords based on words from dictionaries, altered words, words based on common names, bands, favorites etc are categorized under weak passwords. In general, weak passwords are less than eight characters in length. People do not want to take the burden of remembering difficult passwords and in turn, lose their valuable data. Keyboard sequences, birth date, vehicle and contact numbers are used as a password by people. In the table below, we show you a list of top 20 passwords used most frequently across the world.
VI. SIMPLE FORMULAE FOR STRONG PASSWORDS
Generally, a good password is one that takes longer than the usual password change interval to crack. The term strong password, however, is beginning to take on the specific meaning of one that uses all possible password strengthening.
Following methods can be followed to strengthen a password:
Use of multiple upper and multiple lower case letters (a-z, A-Z), use of numbers (0-9), use of multiple special characters (!,*,$,…) and control character(e.g., ^s, Ctrl-s). A strong password should always be at least eight characters in length. The intent of a strong password is to make the password harder to guess, and thus more secure. The password should not be a word in a language, slang, dialect, jargon but a passphrase. A passphrase is a group of alphabets with a possible combination of numbers and special characters which has is no meaning in a dictionary. yppvpp34 is an example of a passphrase. Passwords should not be related to any personal information or identification. One should keep changing his/her password at an interval of time and should not record the password anywhere. Also, monitor for possible eavesdroppers during entry of a password. Though prevention is better than cure if your password is stolen, change the password immediately.
VII. ADD-ONS TO PASSWORD SECURITY
A. Salt
Have you ever imagined food without salt? How would it be? It will be tasteless, undoubtedly. Salt to password adds same as salt to food. For security purposes, passwords are not stored in their clear text form. Instead, a one-way function known as a hash function is applied to the password, possibly in combination with other data (known as a salt), and the resulting value is stored. When a user attempts to use their password to authenticate them, the same hash function is applied and the resulting value is compared with the original stored value. This is a method of encrypting the password which makes life difficult for the hackers. The benefits of precomputation and memorization can be nullified by randomizing the hashing process. This is known as salting. When the user sets a password, a short, random string called the salt is suffixed to the password before encrypting it; the salt is stored along with the encrypted password so that it can be used during verification. Since the salt is usually different for each user, the attacker can no longer construct tables with a single encrypted version of each candidate password. However, if the salt is long enough, there are too many possibilities and the attacker must repeat the encryption of every guess for each user. Modern methods such as message digest5-crypt and bcrypt use salts of 48 and 128 bits respectively. Smart users use salt encryption for their passwords adding more to their security.
B. Shadow
In computing, operating systems use the shadow password database mechanism to increase the security level of passwords by restricting all but highly privileged users’ access to encrypted password data. Typically, that data is kept in files owned by and accessible only by the administrator. Systems administrators can reduce the likelihood of such brute force attacks by making the list of hashed passwords unreadable by unprivileged users. The obvious way to do this is to make the password database itself readable only by the root user. However, this would restrict access to other data in the file such as username-to- user id mappings, which would break many existing utilities and provisions. One solution is a “shadow” password file to hold the password hashes separate from the other data in the world-readable password file. Shadow files mostly contain salt and hashed passwords, the file also contains other fields as well, such as the last time the password was changed, when the password will expire, and whether the account is disabled. The shadow password file does not entirely solve the problem of attacker access to hashed passwords, as some network authentication schemes operate by transmitting the encrypted password over the network making it vulnerable to interception but it reduces the chances of passwords getting hacked to a great extent.
IX. WHAT IF THE PASSWORD IS STOLEN OR CAPTURED
Take a thousand measures to save your password, but there is no assurance to keep it safe. You can protect your passwords to some extent but cannot avoid the theft completely.
Here is a list of few measures taken if you land somewhere wrong.
- If you believe there is a risk your password/s have been captured by another person (accidentally or deliberately) change the affected password/s immediately.
- If you believe there is a risk your passwords have become compromised due to malware, immediately change your passwords for all of your online accounts on a different, uninfected computer. Do not enter any passwords on your computer until it has been cleaned of malware. If you enter your new passwords on your infected computer, they will be immediately captured in the same way as the old passwords. Refer to professionals that will help you to remove malware from your computer.
- In all situations of a suspected compromise of your passwords, you should notify the organization affected, if warranted. For example, if a password is for your online bank account, notify your bank; if a password gives access to your email and your Internet access, notify your Internet Service Provider.
- Always give priority to changing the passwords for those accounts which are most important and valuable.
X. Conclusion
We, the authors present you the necessity of password protection in the daily life. Password protection is first and sometimes the last line of defense. We hereby try to aware the mass about some of the possible threats to passwords and measures to prevent them from being hacked or stolen. Password cracking programs are growing in number and there are many discussions pertaining to their legality. The problem is not their existence but the misuse of them. Bait is thrown, few people try to have it and get into the trap. One should make a habit of using strong passwords which reduce the probability of password being hacked. Passwords should never be recycled. Hope fully this paper will enlighten your views and provide some grip in acquiring more information about particular in depth information. There are several ways by which the password can be hacked, only awareness and precautions can help from being hacked.