In the near future, a pervasive computing environment can be expected based on the recent progress and advances in computing and communication technologies. The next generation of mobile communication will include both popular infrastructured wireless networks and novel infrastructure-less mobile ad hoc networks (MANETs). A MANET is a collection of wireless nodes that can dynamically form a network to exchange information without using any pre-existing fixed network infrastructure. Wireless ad-hoc networks are increasingly being used in the battlefield, emergency search, and rescue missions. The special features of MANET bring great opportunities together with severe challenges. This report describes the concept, features, status, and fundamental problems of ad-hoc networking.
Introduction
Our future living environments are likely to be based on information resources provided by the connections of various communication networks for users. New small devices like Personal Digital Assistants (PDAs), mobile phones, and laptops enhance information processing and accessing capabilities with mobility. To cater to the needs of such devices, modern technologies should adopt a new model of pervasive computing including new architectures, standards, devices, services, tools, and protocols.
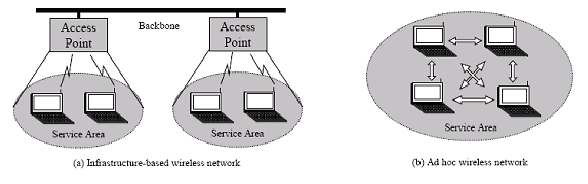
Mobile computing is one of the most important technologies supporting pervasive computing. Advances in both hardware and software techniques have enabled the spread of mobile hosts and wireless networking to the masses. Generally, there are two modes in which wireless mobile nodes can communicate:
- Infrastructured: In this mode, all the communication among the mobile nodes goes through a base station. A Base station is also known as an access point. These base stations are connected to fixed infrastructure or wired networks.
- Infrastructureless: This mode of communication is known as a mobile ad hoc network. A MANET is a collection of wireless nodes that can dynamically form a network to exchange information without using any pre-existing fixed network infrastructure. This is a very important part of communication technology that supports truly pervasive computing because in many contexts information exchange between mobile units cannot rely on any fixed network infrastructure, but on the rapid configuration of wireless connection on-the-fly. A typical example of this mode of communication is people sitting in a conference room and exchanging data among themselves without any fixed infrastructure.
Suggested Read:
• Mobile ad-hoc network routing protocols and applications
• Security aspects in mobile-ad hoc networks
Related Background
MANET Concept
A mobile ad-hoc network is a collection of wireless nodes that can dynamically be set up anywhere and anytime without using any pre-existing network infrastructure. It is an autonomous system in which mobile hosts connected by wireless links are free to move randomly. In MANET, nodes act both as host and routers. The traffic types in ad hoc networks are quite different from those in an infrastructured wireless network, including:
- Peer-to-Peer: Communication between two nodes, which are within one hop.
- Remote-to-Remote: Communication between two nodes beyond a single hop but which maintain a stable route between them. This may be the result of several nodes staying within communication range of each other in a single area or possibly moving as a group. The traffic is similar to standard network traffic.
- Dynamic Traffic: This occurs when nodes are dynamic and moving around. Routes must be reconstructed. This results in a poor connectivity and network activity in short bursts.
MANET Features
MANET has the following features:
- Autonomous terminal: In MANET, each mobile host is an autonomous node, which may function as both a host and a router. In other words, besides the basic processing ability as a host, the mobile nodes can also perform switching functions as a router. So usually endpoints and switches are indistinguishable in MANET.
- Distributed operation: Since there is no background network for the central control of the network operations, the control, and management of the network is distributed among the terminals. The nodes involved in a MANET should collaborate amongst themselves and each node acts as a relay as needed, to implement functions e.g. security and routing.
- Multi-hop routing: Basic types of ad hoc routing algorithms can be single-hop and multi-hop. Single-hop MANET is simpler than multihop in terms of structure and implementation, with the cost of lesser functionality and applicability. When delivering data packets from a source to its destination out of the direct wireless transmission range, the packets should be forwarded via one or more intermediate nodes.
- Dynamic network topology: Since the nodes are mobile, the network topology may change rapidly and unpredictably and the connectivity among the terminals may vary with time. MANET should adapt to the traffic and propagation conditions as well as the mobility patterns of the mobile network nodes. The mobile nodes in the network dynamically establish routing among themselves as they move about, forming their own network on the fly. Moreover, a user in the MANET may not only operate within the ad hoc network but may require access to a public fixed network.
- Fluctuating link capacity: The nature of high bit-error rates of wireless connection might be more profound in a MANET. One end-to-end path can be shared by several sessions. The channel over which the terminals communicate is subject to noise, fading, and interference, and has less bandwidth than a wired network. In some scenarios, the path between any pair of users can traverse multiple wireless links and the link themselves can be heterogeneous. One effect of the relatively low to moderate capacities is that congestion is typically the norm rather than the exception i.e. aggregate application demand will likely approach or exceed network capacity frequently.
- Energy-constrained operation: Some or all of the nodes in a MANET may rely on batteries or other means for their energy. Such devices need optimized algorithms and mechanisms that implement computing and communicating functions.
- Limited physical security: MANETs are generally more prone to physical security threats than are fixed cable networks. The increased possibility of eavesdropping, spoofing and denial-of-service attacks should be carefully considered.
MANET Status
Ad hoc network is not a new concept. It was first deployed in the military in the 1970s. Commercial interest in such networks has grown recently due to the advancement in wireless communication. A new working group for MANET has been formed within the Internet Engineering Task Force (IETF) to investigate and develop standards for Internet routing support for mobile, wireless IP autonomous segments and develop a framework for running IP-based protocols in ad hoc networks.
The recent IEEE standard 802.11 has increased the research interest in the field. Many international conferences and workshops have been held by e.g. IEEE and ACM. For instance, MobiHoc (The ACM Symposium on Mobile Ad Hoc Networking & Computing) has been one of the most important conferences of ACM SIGMOBILE (Special Interest Group on Mobility of Systems, Users, Data, and Computing). Research in the area of ad hoc networking is receiving more attention from academia, industry, and government. Since these networks pose many complex issues, there are many open problems for research and significant contributions.
Challenges in Mobile Ad hoc Networks
The special features of MANET bring this technology to great opportunity together with severe challenges. These include:
Routing in MANETs
The main function of the network layer is routing packets from the source machine to the destination machine. The routing algorithm is that part of the network layer software responsible for deciding which output line as incoming packet should be transmitted on. The algorithms that choose the routes and the data structures that they use are major areas of network layer design.
What makes routing algorithms a challenging task in the ad hoc network when there are lots of algorithms available for the wired network?
The reason is the changing topology of the ad hoc networks. All the rules of wired networks i.e. fixed topologies, fixed and known neighbors are automatically becoming out of scope. With an ad hoc network, the topology may be changing all the time; so valid routes can change spontaneously without any warning.
The following are the desirable properties of MANET routing protocol:
- Distributed operation: Since there is no central point like a wired network, each and every node in the MANET performs routing.
- Loop-freedom: Though, if not incorporated in the routing protocol, the TTL value could be used to prevent the packet from roaming in the network for arbitrarily long periods of time. But, still, this property is desirable for efficient use of resources and better overall performance.
- Demand-based operation: Instead of assuming a uniform traffic distribution within the network and maintaining routing information between all nodes at all times, routing algorithm should adapt to the traffic pattern on a demand or need basis. It should be done in such a way so that it could utilize mobile nodes energy and network bandwidth more efficiently at the cost of increased route discovery delay.
- Proactive operation: This is the opposite of demand-based operation. It certain contexts, the additional latency demand-based operation are unacceptable. If bandwidth and energy resources permit, the proactive operation is desirable in these contexts.
- Security: Without some form of network-level or link layer security, a MANET routing protocol is vulnerable to many forms of attack. It may be relatively simple to snoop network traffic, manipulate packet headers and redirect routing messages, within a wireless network without appropriate security provisions.
- Sleep period operation: As a result of energy conservation, or some other need to be inactive, nodes of a MANET may stop transmitting and/or receiving for arbitrary time periods. A routing protocol should be able to accommodate such sleep periods without overly adverse consequences.
- Unidirectional link support: Bi-directional links are typically assumed in the design of routing algorithms, and many algorithms are incapable of functioning properly over unidirectional links. But, unidirectional links can and do occur in wireless networks.
Conclusion
MANET is one of the most important and essential technologies in current times. Mobile ad hoc networks can be exploited in a wide area of applications, from the military, emergency rescue, law enforcement, and commercial, to local and personal contexts. It has already gained critical mass among researchers in academia as well as in industry. Moreover, there is also a flurry of activity in the standards bodies in this area. Many routing protocols designed for ad hoc networks have been proposed as Internet-Draft and Request for Comments (RFC) of Internet Engineering Task Force (IETF). However, MANET as a technology can only become successful and popular if the challenges related to routing and intrusion detection are adequately addressed.
Sir wearable biosensor. Topic is latest or not?
Yes. There have been many advancements in the field of wearable biosensors recently.
Hello sir,
I want some latest seminar topics for information technology. Please give me latest topic it’s very urgent please sir.
Hi Pallavi,
You can go through following.
1. Wearable biosensors – https://krazytech.com/technical-papers/wearable-biosensors
2. Machine learning
3. Speech Recognition – https://krazytech.com/technical-papers/speech-recognition
More – https://krazytech.com/technical-papers/technical-topics-for-paper-presentation-2017
Please sir can you help me on how to implement cooperative black hole nodes detection in Manets using NS2.35.